
telegram members
twitter followers

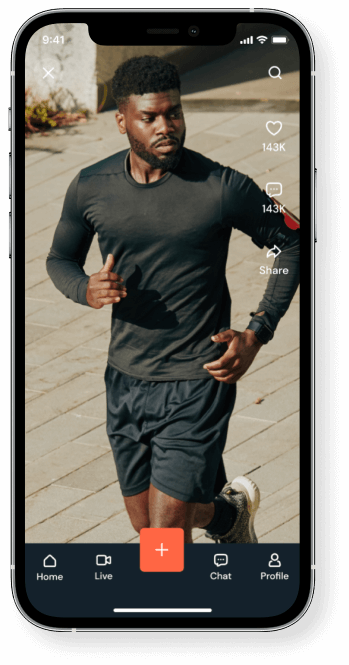
Navigation
We have a very enthusiastic community that genuinely enjoys finding & collecting coins on our platform.
Tracking Time
We have a very enthusiastic community that genuinely enjoys finding & collecting coins on our platform.
Activities
We have a very enthusiastic community that genuinely enjoys finding & collecting coins on our platform.
Count Coins
We have a very enthusiastic community that genuinely enjoys finding & collecting coins on our platform.

DISTANCE RUN (km)

calories burned
You Can Determine Your Earning
It’s a fun and interactive way to learn about various cryptocurrency projects in the space.
The Roadmap
The input material for the recovery process consists of sintered hard tungsten carbide scrap, as well as soft scrap such as powders
The Concept was Born
Mockup & App Design
Web Development
Community Event
Our Team
The input material for the recovery process consists of sintered hard tungsten carbide scrap, as well as soft scrap such as powders
Joey Wong
Morgan Cooper
Kenneth Chau
Andry Hall
Carol Lee
Jared Nilson
Matilda Brown

Read FAQ`s
Will Ridius launch NFTs?
Through our years of experience, we've also learned that while each channel has its own set of advantages, they all work best when strategically paired with other channels.
Does Ridius have a token?
Through our years of experience, we've also learned that while each channel has its own set of advantages, they all work best when strategically paired with other channels.
Do I have to buy an NFT to move2earn?
Through our years of experience, we've also learned that while each channel has its own set of advantages, they all work best when strategically paired with other channels.
How I can join a challenge?
Through our years of experience, we've also learned that while each channel has its own set of advantages, they all work best when strategically paired with other channels.
Latest News
The input material for the recovery process consists of sintered hard tungsten carbide scrap, as well as soft scrap such as powders